Security Validation Platform for Enterprises
A suite of integrated security tools designed to assess and strengthen an enterprise’s security posture. The platform identifies vulnerabilities in systems and processes, recommends security frameworks and architecture improvements, and integrates seamlessly into existing enterprise structures, ensuring robust protection, compliance, and scalable security management.
Technical stack includes:
-
Backend: Java, Spring Boot, Hibernate, Spark, PostgreSQL, Cassandra, MongoDB, Redis, Kafka, Selenium
-
Frontend: ReactJS, Redux, Material UI, HTML5, CSS3
-
Infrastructure & DevOps: AWS, Jenkins, Kubernetes, Docker, Kibana
The goal
The client approached us to develop a system to automate enterprise security audits. With years of experience in the field, they had a clear vision for the product’s first version. Their team included a CTO and a security audit expert, but no skilled developers.
The MVP
To refine their requirements, we engaged a requirements analyst and UI/UX designer to create a precise specification for the MVP. In just three weeks, their initial ideas were transformed into a detailed development plan, with UI/UX designs completed in two weeks.
The collaboration
Our team developed the MVP over four months, enabling the client to start using it with early adopters immediately. We continued supporting and enhancing the product for 1.5 years, implementing features according to the client’s roadmap.
The team
The development team included nine specialists: a project manager/requirements analyst, two front-end developers, two back-end developers, one DevOps engineer, one UI/UX designer, and two QA engineers. Later, the team was streamlined to five experts during the support phase.
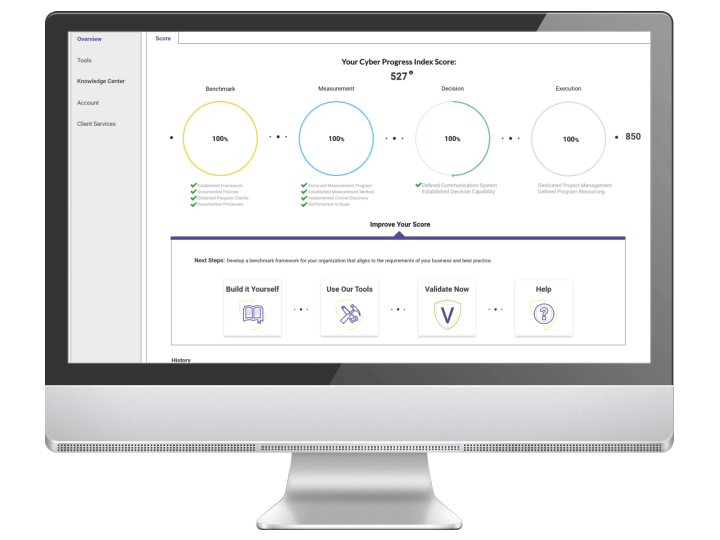
Security Program Assessment
The platform provides a comprehensive evaluation of the client’s security landscape, including:
- Technology & Applications: Analysis of software, systems, and service configurations
- Network & Infrastructure: Review of network architecture, connectivity, and endpoint security
- Processes & Policies: Assessment of operational procedures, compliance frameworks, and governance
- Risk & Gap Analysis: Identification of vulnerabilities, threats, and areas for improvement
Based on the assessment, the platform generates a multi-year roadmap to guide the enterprise toward an optimized, future-ready security program.
Delivered Results
- Comprehensive security visibility – Enterprises can identify gaps in policies, processes, and architecture across multiple systems
- Automated compliance assessment – Reduced manual effort in auditing and adherence to security frameworks
- Improved incident response – Real-time monitoring and alerts reduced detection and mitigation time
- Scalable and maintainable platform – Designed to grow with enterprise needs while maintaining high security standards
- Enhanced confidence in security posture – Demonstrated compliance and proactive risk management to stakeholders
Get Insights from Real SaaS Builds
Enjoyed the read? We write these case studies and articles to share what works — and what doesn’t — in real SaaS delivery. Got a challenge of your own? Let’s talk tech.

Ryzhokhin